逆向工程是一件複雜而漫長的工作,選用對的工具為您完成,節省寶貴的時間。
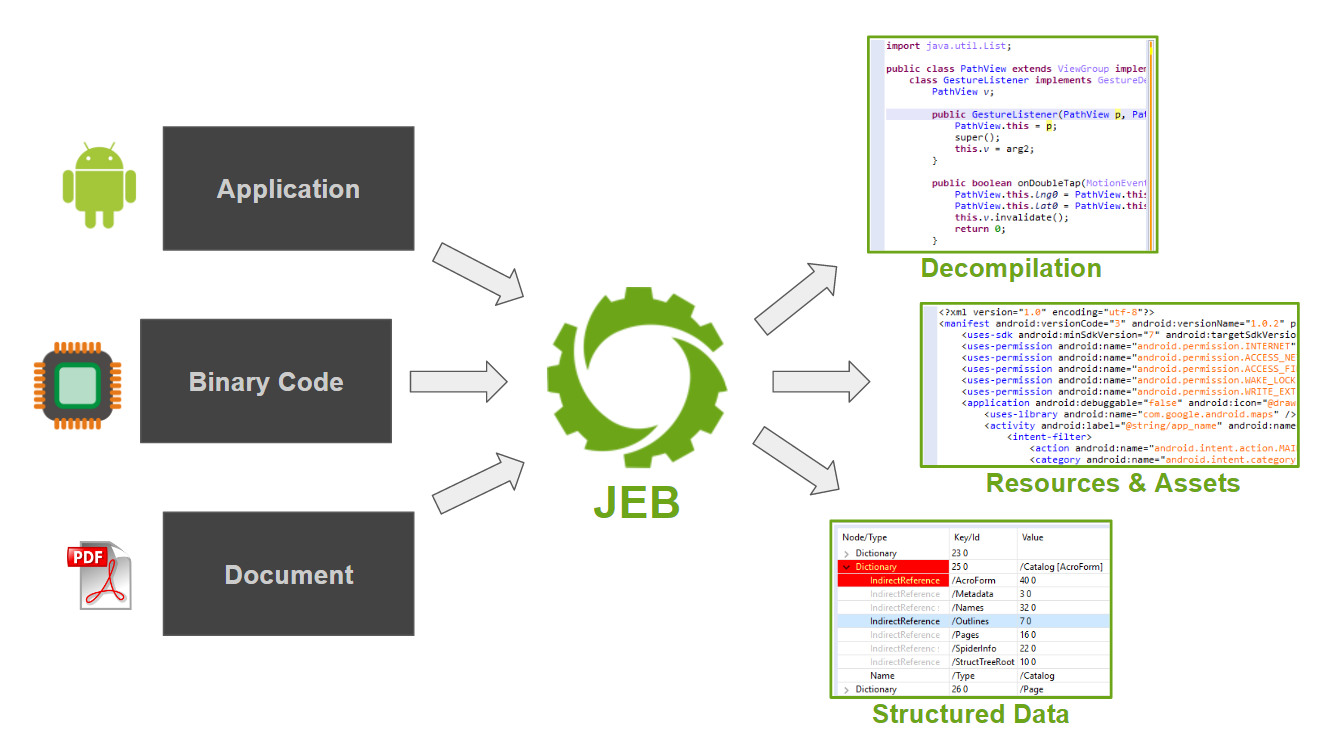
JEB 是一套為專業工程師設計的模組化逆向工程平台。它的功能豐富,讓工程師執行disassembly,decompilation,debugging,以及分析程式碼或文件檔案。您可對程式手動執行工作,或是將它排程入軟體分析自動執行。
- The Android modules for JEB provide static and dynamic analysis capabilities to analyze Android applications, goodware or badware, small or large.
- The native code analysis modules provide advanced code analyzers and decompilers for MIPS, ARM and ARM64, Intel x86 and x64 processors, as well as WebAssembly modules and Ethereum smart contracts
- Our PDF module for JEB is the most complete PDF document analyzer in the industry. Use it to manually or automatically reverse engineer documents.
Android Decompiler + Android Debuggers
Use JEB to perform reverse engineering of malicious APKs and security audits.
Cut down on costly reverse engineering time: decompile obfuscated APKs, examine Java code and debug closed-source apps in minutes. Our modular back-end, coupled with a powerful UI front-end for desktop platforms, allow refactoring operation and scripting to automate complex tasks.
Perform static and dynamic analysis of Android applications, goodware or badware, small or large.
- Decompile code using our Dalvik decompiler, including multi-dex APK.
- Refactor the analysis to defeat obfuscated code generated by application protectors.
- Reconstruct resources and obfuscated XML files.
- Debug Dalvik code as well as all native code (Intel, ARM), seamlessly.
- Automate and script your reverse engineering tasks via our API.
Powerful
Perform precise and robust decompilation of Android apps and Dalvik bytecode.
Our in-house decompiler works on true Dalvik code: conversion from Dex to Jar, required by free tools, is not necessary with JEB (see why it matters).
Our Dalvik and native code debuggers offer unmatched features to seamlessly analyze real-time apps, allowing examination of code and hooking of sensitive APIs.
Flexible
Refactor, annotate, navigate, and modify the analysis output.Our analysis modules support code refactoring, virtual hierarchy to organize highly obfuscated code, or code cleaning (for instance when decrypting obfuscated contents or un-reflecting code).
Extensible
Leverage the JEB API to automate reverse engineering tasks.
Using Java or Python, users can write their own scripts and plugins to automate the reverse engineering process. Power users can write full-blown analysis modules and headless front-ends.
ARM Decompiler
Use JEB to reverse engineer programs and malware written for ARM platforms.
Our ARM machine code decompiler allows reverse engineers and security auditors to analyze malicious ARM binary files.
The ARM decompiler provides the following features:
- Augmented disassembly including resolution of dynamic callsites and syscalls, candidate values determination for registers, dynamic cross-references, etc.
- Decompilation of ARM 32-bit and ARM-Thumb code to pseudo-C source code.
- Advanced optimization passes to thwart protected or obfuscated code.
- Interactive layer allowing refactoring: type definition, stackframe building, renaming/commenting/cross-referencing, etc.
- Full API to perform advanced and/or automated code analysis in Python or Java.
MIPS Decompiler
Use JEB to reverse engineer MIPS embedded programs and malware.
Our MIPS processor and microcontroller machine code decompiler allows reverse engineers and security auditors to analyze malicious MIPS programs and audit complex embedded systems (routers, set-top boxes, IOT devices, etc.).
The MIPS decompiler provides the following unmatched features:
- Augmented disassembly including resolution of dynamic callsites and syscalls, candidate values determination for registers, dynamic cross-references, etc.
- Decompilation of MIPS 32-bit to pseudo-C source code.
- Advanced optimization passes to thwart protected or obfuscated code.
- Interactive layer allowing refactoring: type definition, stackframe building, renaming/commenting/cross-referencing, etc.
- Full API to perform advanced and/or automated code analysis in Python or Java.
Intel Decompiler
Use JEB to reverse engineer x86 32-bit and x86 64-bit programs and malware.
Our Intel x86 and Intel x86-64 decompilers are part of JEB 3 Pro and Pro Floating.
The x86 decompiler and x86-64 decompiler provide the following features:
- Augmented disassembly including resolution of dynamic callsites, candidate values determination for registers, dynamic cross-references, etc.
- Decompilation of x86 and x86-64 to pseudo-C source code.
- Partial Class Recovery and Decompilation to C++ for programs compiled with MS VCPP (see video).
- Advanced optimization passes to thwart protected or obfuscated code.
- Win32 type libraries and common signatures for efficient Windows file analysis.
- Interactive layer allowing refactoring: type definition, stackframe building, renaming/commenting/cross-referencing, etc.
- Full API and access to the Intermediate Representations to perform advanced and/or automated code analysis in Python or Java.
WebAssembly Decompiler
Use JEB to reverse engineer WebAssembly binary modules.
The WebAssembly plugins provide the following features:
- Augmented disassembly and parsing of wasm binary modules.
- Decompilation of wasm bytecode to pseudo-C source code.
- Advanced optimization passes to thwart protected or obfuscated code.
- Interactive layer for typing/renaming/commenting/cross-referencing, etc.
- Full API access for scripting and plugins.
JEB WebAssembly plugins can also be used to decompile Smart Contracts compiled to wasm, such as EOS or Parity contracts.
Ethereum Decompiler
Use JEB to reverse engineer Ethereum opaque smart contracts and dApps to Solidity-like high-level code.
Cut down on costly reverse engineering time: decompile Ethereum smart contracts to Solidity-like source code to easily understand and review closed-source contracts and dApps.
- Decompile EVM contract code to Solidity-like high-level code using our Ethereum decompiler.
- Annotate the analysis results to better understand what the compiled contract or dApp is doing.
- Automate or script your reverse engineering tasks via our API.
PDF Document Analyzer
Analyze malicious Adobe™ PDF files using the best PDF document analyzer in the industry.
Our PDF module breaks down and decodes PDF files to provide access to its inner components such as resources and scripts. It detect structure corruptions and issues notifications to report suspicious areas. Leverage the PDF module either through the desktop client or a headless client, such as a file analyzer stack or automation pipeline.
Use our PDF analyzer to manually or automatically reverse engineer documents of all sizes.
- Break-down the PDF structure into a visually compelling and navigable tree.
- Deal with corrupt files, complex streams (eg, multiple encodings, etc.).
- Retrieve 20+ notifications and alerts generated by the analyzer to pin-point suspicious areas and use them to issue a determination on the file.
- Extract embedded Javascript even in the most extreme cases.
- Automate the reverse engineering process via the JEB API to perform bulk analysis.
Analyze Anything
Leverage the JEB API to write custom modules to handle virtually any file type.
We do provide training for power‑users that wish to use the API to its full extent.
Our community of users also share free open‑source modules, plugins, scripts and tutorials for developers.
Software Package
The software package is distributed as a zip archive, custom-generated for each registered user. It contains the back-end components as well as the reference front-end implementation for desktop platforms, referred to as the UI client through the rest of this manual. This manual focuses mostly on using JEB through the UI client.
The UI client runs on the following platforms:
- Windows (x64)
- Linux/GTK (x64, arm64)
- macOS (x64, arm64)
Requirements
JEB requires a Java SE Development Kit (JDK):
- JEB GUI client: JDK 17
- Command-line client: JDK 11 or above
Java 18+
Java 18 or above is not recommended at the time of writing.
版本介紹
| License Type |
JEB Android
|
JEB Pro
|
JEB Pro Floating
|
|
List of analysis modules
|
Android modules | All modules | All modules |
|
JEB with official UI client
|
V | V | V |
|
Support for extensions
(plugins and scripts) |
V | V | V |
|
Work without an Internet connectio
|
V | V | |
| Execute third-party front-end clients | V | V | |
|
Floating seats
|
V |
版本比較表
| Build Type > | JEB CE Community Edition |
JEB Android | JEB Pro |
| Base | |||
| Suitable for enterprise or professional use | V | ||
| Decompilers | |||
| Dalvik Decompiler | V | V | |
| Deobfuscation module for "virtualized" code | V | ||
| Advanced deobfuscators requiring native code emulation (JNI) | V | ||
| Java Decompiler | V | V | |
| Intel x86 Decompiler | V | V | |
| Intel x86-64 Decompiler | V | V | |
| ARM Decompiler | V | V | |
| ARM64 Decompiler | V | V | |
| MIPS Decompiler | V | ||
| MIPS64 Decompiler | V | ||
| RISC-V Decompiler | V | ||
| WebAssembly Decompiler | V | ||
| Ethereum Decompiler for Smart Contracts (EVM Decompiler) | V | ||
| Diem (Libra) Decompiler for Move modules (open-sourced) | V | ||
| Base Plugins | |||
| Archive files (zip, 7z, tar) | V | V | V |
| Image files (bmp, png, jpg, gif, ico) | V | V | V |
| Structured text files (html, xml, json) | V | V | V |
| Certificate files (x.509) | V | V | V |
| Application Processors | |||
| Android APK (incl. dex, odex, x-apk) | V | V | V |
| Windows PE/PE64/COFF, PDB | V | V | V |
| Linux ELF/ELF64 | V | V | V |
| Mach-O, Mach-O/FAT | V | V | V |
| Intel HEX (ihex) | V | V | V |
| Chrome Extension (crx) | V | V | V |
| WebAssembly module (wasm) | V | V | |
| Ethereum contracts (evm) | V | V | |
| Disassemblers | |||
| Dalvik Disassembler | V | V | V |
| Intel x86 Disassembler | V | V | V |
| Intel x86-64 (AMD64) Disassembler | V | V | V |
| ARM (32, Thumb) Disassembler | V | V | V |
| ARM64 (Aarch64) Disassembler | V | V | V |
| MIPS Disassembler | V | V | V |
| RISC-V Disassembler | V | V | V |
| Atmel AVR 8-bit Disassembler | V | V | V |
| Miscellaneous Binary Parser Plugins | |||
| Flutter/Dart AOT Snapshot Parser | V | V | V |
| Debuggers | |||
| Dalvik Debugger (Android) | V | V | |
| Intel x86 Debugger (GDB/LLDB all platforms, incl. Android) | V | V | V |
| Intel x86-64 Debugger (GDB/LLDB all platforms, incl. Android) | V | V | V |
| ARM Debugger (GDB/LLDB all platforms, incl. Android) | V | V | |
| ARM64 Debugger (GDB/LLDB all platforms, incl. Android) | V | V | |
| MIPS Debugger (GDB/LLDB all platforms, incl. Android) | V | V | |
| Document Parsers | |||
| Adobe PDF | V | ||
| FAT file systems (file access table) | V | V(plugin) | |
| Platform | |||
| Persist JEB Projects to JDB2 Databases | V | V | V |
| Interactivity (refactoring, renaming, commenting, etc.) | V | V | V |
| Graphing (CFG, Callgraphs, etc.) | V | V | V |
| Support for multiple Artifacts in a same Project | V | V | |
| Extensions - Client scripts in Python | V | V | V |
| Extensions - Back-end plugins in Java | V | V | V |
| Automation / headless launcher | V | ||
| Work offline | V | ||

.png)